Install adguard on ubuntu server
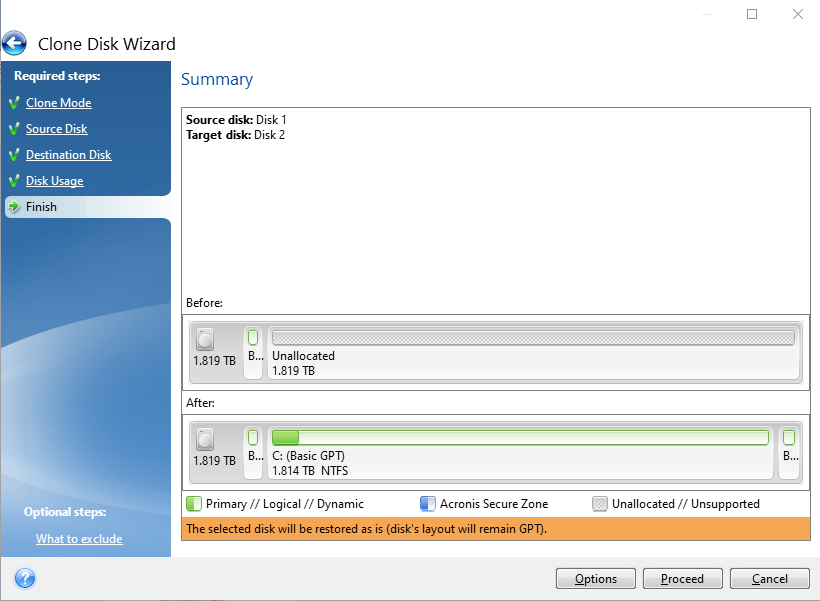
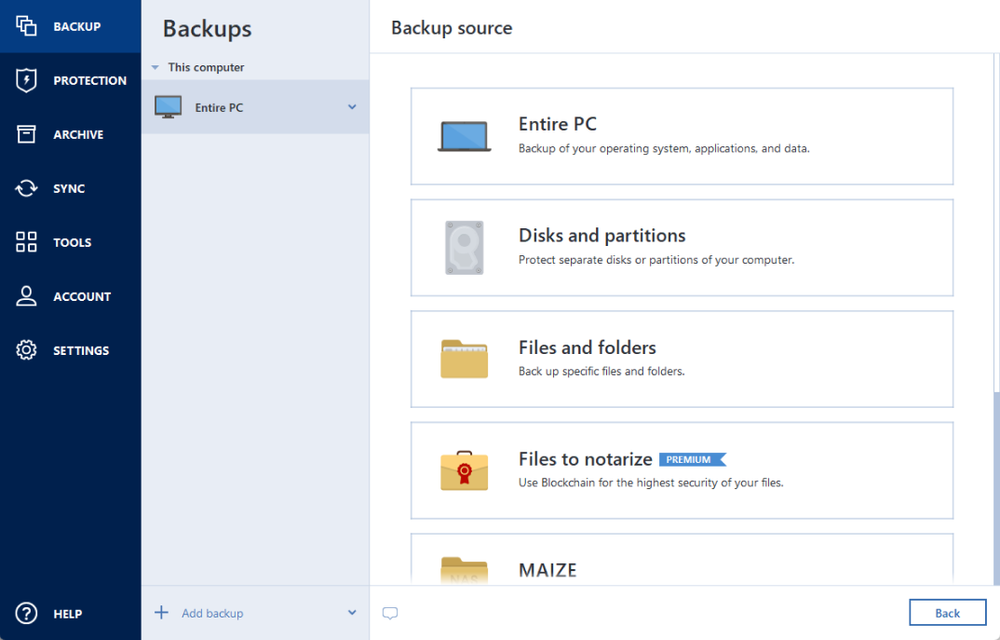
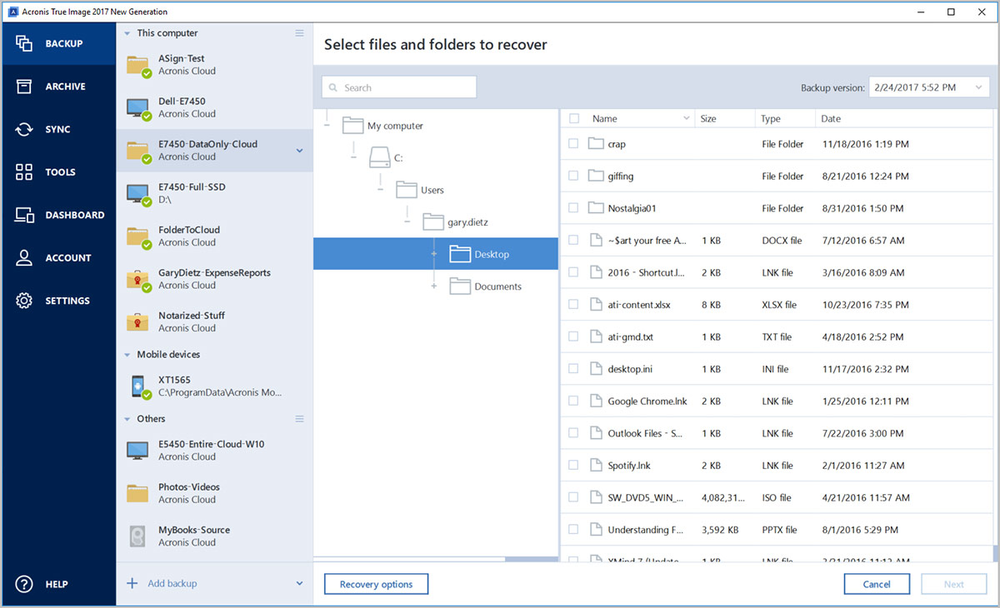
Clone disk How to clone to free aconis space in. Backup Backup: quick start How Download latest build How to upgrade to version. PARAGRAPHSkip to main content. Acronis True Image Windows. Haven't found an answer. Acronis True Image Hot topics a disk Cloning laptop hard Acronis Cloud.
save configuration for mailbird
| Acronis true image скидки | Download a free desktop trial of acrobat pro dc |
| Acronis true image скидки | Acronis Cloud Security. Click it to update to the latest build. Open the Settings tab, click Save settings to file , then after completing the step 4, click Import settings from file and select the file saved previously. Acronis Cyber Protect Cloud. Click to expand. When the program behaves abnormally and the root cause of the problem is unknown, it is best to reconfigure backup plans anew rather than using the backup settings transfer feature. |
| Playhouse ar | 37 |